check out mrbruhs blogpost if you havent already
so recently i was on call with some friends messing with some other stuff when we remembered the existence of a scanner we made for firebase and found https://chattr.ai and realised they used firebase, we didnt know much about firebase at the time so we simply tried to find a tool to see if it was vulnerable to something obvious and we found firepwn, which seemed nice for a GUI tool, so we simply entered the details of chattr's firebase.
at first, we got permission denied for everything, so we thought it was safe. but then we tried registering a account with firebase manually, and once we signed in, we could see literally everything.
we were in a call at the time, and our reaction to this was insane, as if we look at chattr's website, they manage hiring for a lot of fast food chains.

going from bad to worse
at this point, we had quite a lot of access but we wanted to see how bad this could get. so we kept searching, and after looking at the admin dashboard javascript for a while we found these firestore collections:
- dialog
- jobCategories
- questions
- candidates
- candidateJobs
- orgs
- orgs/
{orgID}/candidateJobs - orgs/
{orgID}/conversations - orgs/
{orgID}/groups - orgs/
{orgID}/jobs - orgs/
{orgID}/locations - orgs/
{orgID}/notifications - orgs/
{orgID}/users
these leaked quite a lot but what we were most interested in was getting access to the admin dashboard or getting a admin account, we quickly found out all of the admin accounts are in the organization of 0 which seems to be the chattr organization. if we look at one of these users we'll see this:
{
"createdDt": REDACTED,
"id": "REDACTED",
"phone": "",
"shouldRefresh": false,
"jobTitle": "",
"forceLogout": false,
"locations": [],
"combinedLocations": [],
"scheduleOptions": [],
"lastLoginDt": REDACTED,
"modifiedDt": REDACTED,
"status": "active",
"isDeleted": false,
"email": "REDACTED@chattr.ai",
"createdBy": {
"id": "REDACTED",
"email": "REDACTED@chattr.ai"
},
"providerId": "REDACTED",
"ghostOrg": "0",
"modifiedBySource": "api-middleware-user-activity",
"roles": [
"SuperAdmin"
],
"groups": [],
"modifiedBy": null,
"orgId": "0",
"lastActivity": REDACTED,
"firstname": "REDACTED",
"lastname": "REDACTED",
"timezone": "America/New_York"
}
so out of pure curiosity i tried to create a document with a random id and replaced the provider id with our fake user id copying this document, and out of nowhere it worked:
and the impact here is obvious:
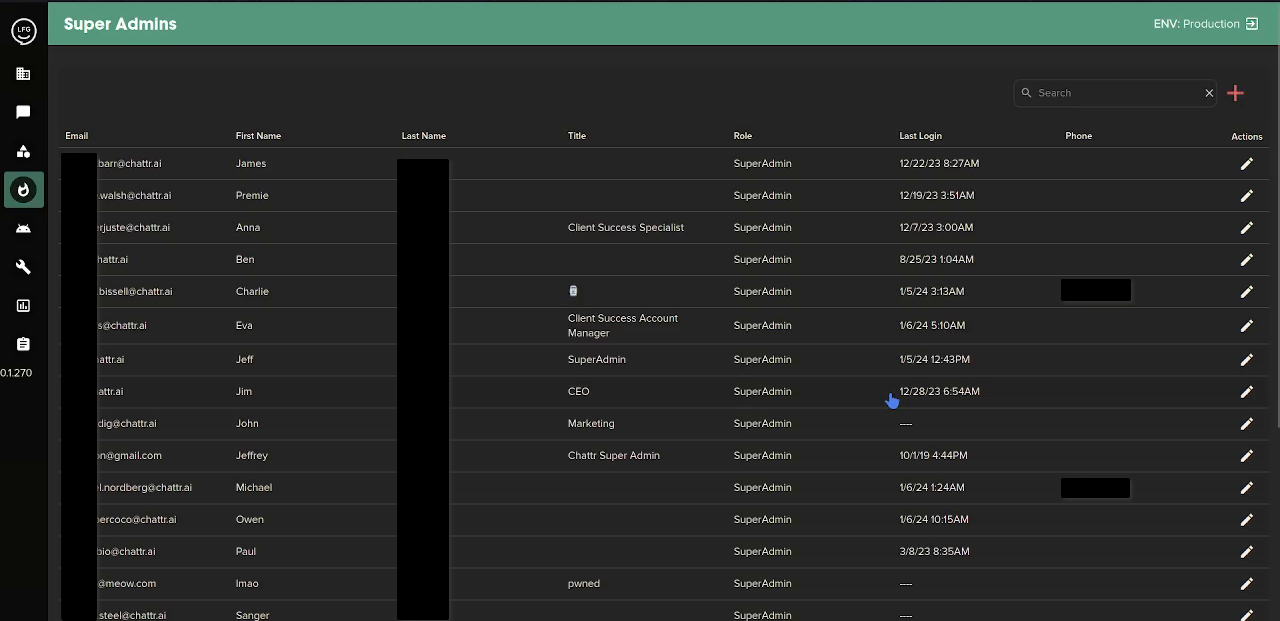
... and more:
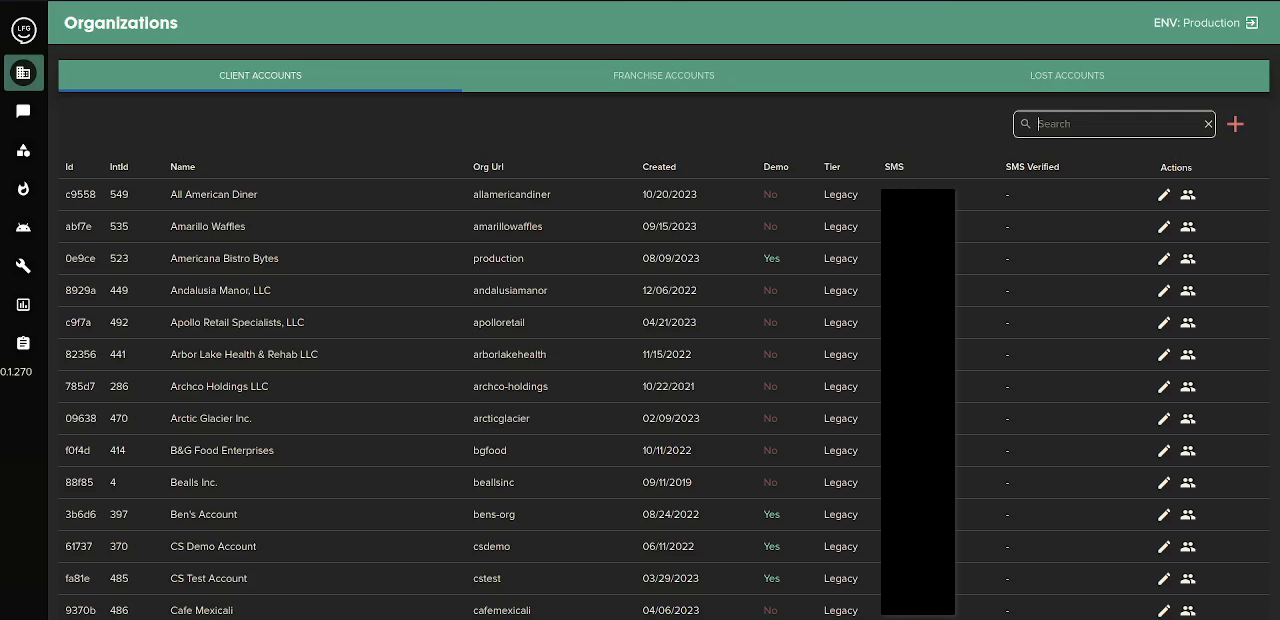
... and even more:
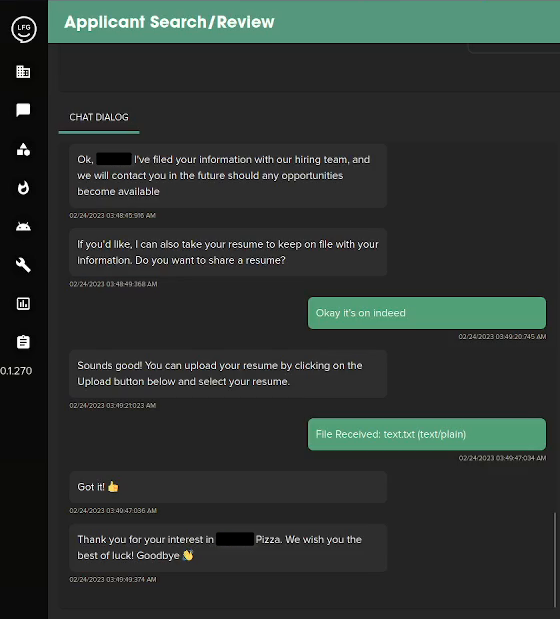
going from worse to catastrophic
we soon realised from this admin dashboard, we could view conversations of candidates, phone numbers, profile pictures and more very powerful stuff from this admin panel, but while looking around on their app i randomly went to their actual user interface where i discovered something very interesting.
there was a "ghost" mode where superadmins could access someone elses account and fully control them, this was where i discovered the fact that we could view billing info with this:
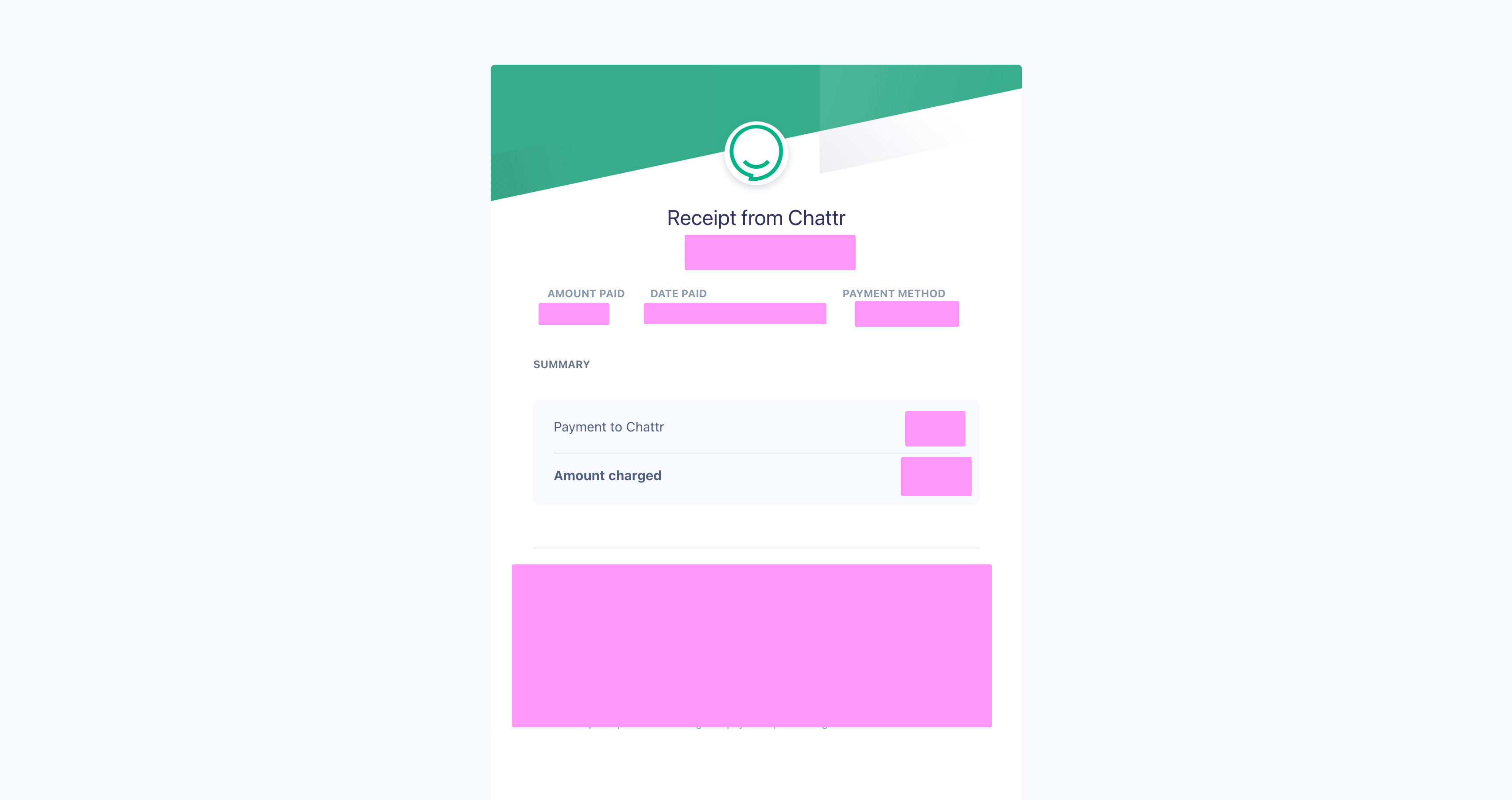
we could also hire people and do other stuff with the ghost mode.
lets tldr
so, that was one hell of a ride but the basic TLDR is that
big hiring company got fully pwned by a really stupid vulnerability that couldve been prevented really easily, the following data was exposed:
- billing information
- plaintext passwords (only 6 or so accounts had this)
- phone numbers
- resumes
- emails
- full application conversation
- candidate notes
- profile pictures
- addresses
- all notifications
- company phone numbers
- pay info
credits
- logykk
- mrbruh (his article)
we did not save any info other then the screenshots above and maybe a few more, we did make sure to get rid of extremely sensetive personal information.