this started when i was looking into cursor, an ai text editor. also, i use lulu by objective-see on my laptop, so when i downloaded the cursor installer, i got this pop-up:
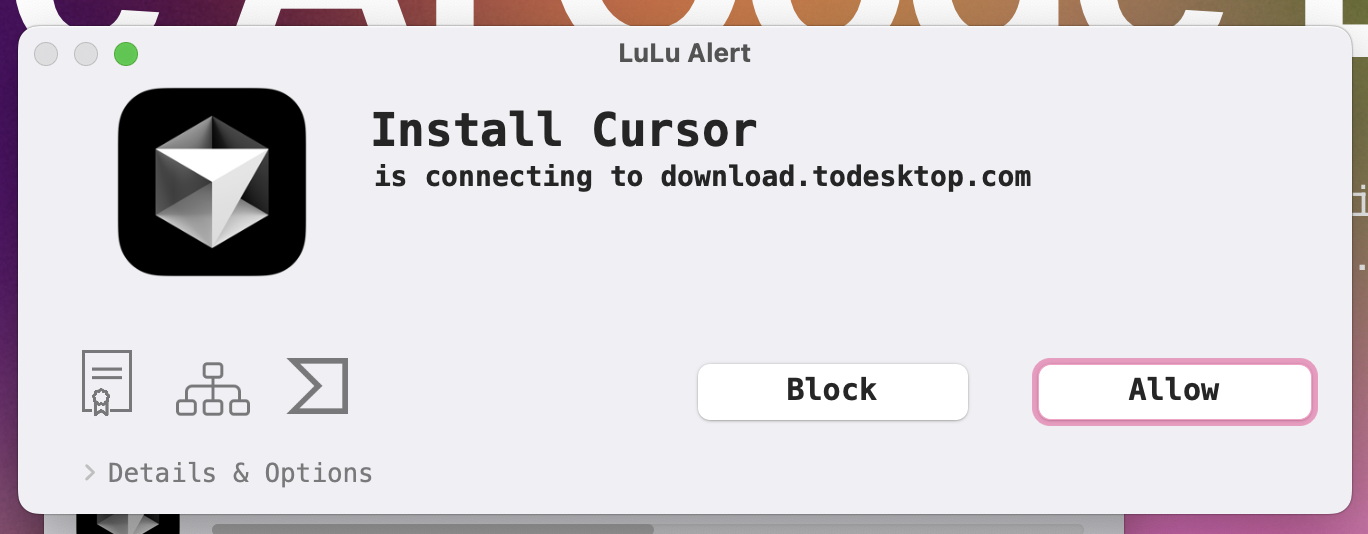
now, what the hell is todesktop? i thought i was downloading cursor? well, looking at their website, they seem to be an electron app bundler service alongside providing a SDK for electron apps. so it appears the installer i downloaded is actually managed by todesktop, not cursor.
this made me curious and i made an account on todesktop to look into it, and when i clicked the github login button, i saw my calling: firebase
basic firebase recon
realising the app used firestore (firebase's no-sql database that is often used in frontend), i quickly opened my devtools and began doing basic recon on the firebase.
i realised that the site has sourcemaps, which made searching for all of the firestore paths used in the app even easier (its still easy without sourcemaps, usually)
then i found an insecure collection, temporaryApplications, which seemed to give me an name list of some applications (edit: todesktop has clarified this collection has no sensitive data and hasnt been updated since 2022), but not much other than that, everything seemed secure on the firebase other then this.
i then noticed that most of the deployment and general logic happens in the terminal, with the npm package @todesktop/cli, so i installed that and started looking into it
looking into the todesktop cli
the cli manages deployments, source code uploads, and much more. the website just seems to be a shell to create applications, view deployments, etc etc
i was once again lucky that the cli also had sourcemaps, so i used sourcemapper to extract them into a source tree.
looking in there, i found an arbitrary s3 upload vulnerability via a firebase cloud function called getSignedURL, but i didn't really have an s3 key (file path) to upload to that would do something interesting, so i kept looking.
hijacking the deployment pipeline via a postinstall script
i wanted to get on the machine where the application gets built and the easiest way to do this would be a postinstall script in package.json, so i did that with a simple reverse shell payload
this worked. navigating around the container, i figured out where the actual code-building application lives, and found this:
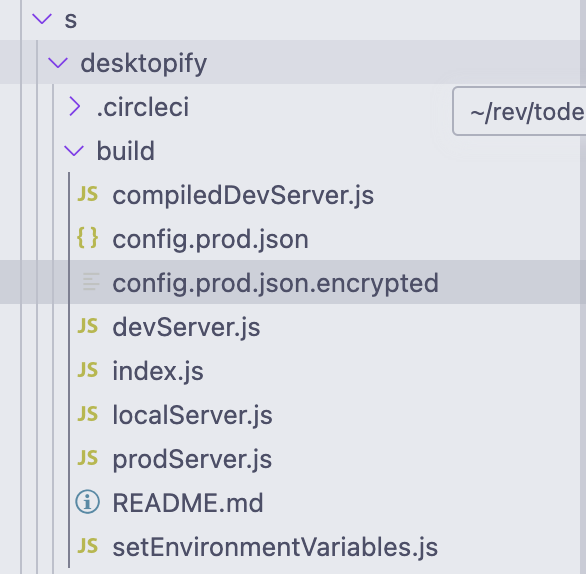
oh fuck, this usually means something bad. i found the code for decrypting this file, and this is what i got after decrypting it myself:
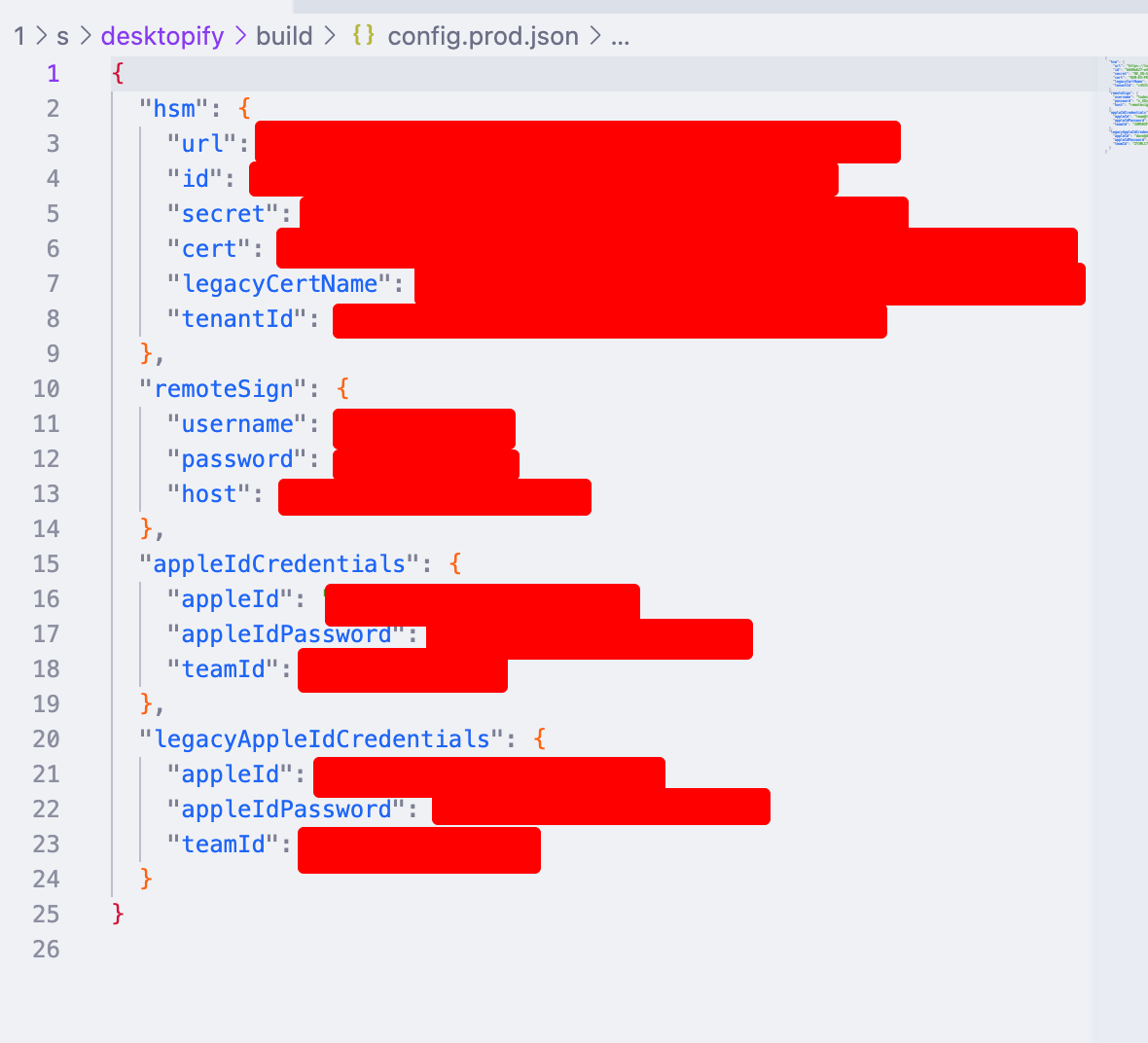
fuck. this container stores secrets
looking around in the container more, i found a hardcoded firebase admin key (which was full-scoped).
post-exploitation
i quickly realized that with the credentials i have, i could deploy an auto update to any app of my liking, having clients receive it immediately when they restart the app.
i then made some code to use my credentials to deploy an update to my app, and it worked. i immediately got a update on my client and got RCE.
lets talk about impact
with this, i could push auto updates to all applications using todesktop, such as:
- clickup (https://clickup.com)
- cursor (https://cursor.com) (update: cursor has now switched off of todesktop to their own build system)
- linear (https://linear.app)
- notion calendar (https://calendar.notion.so)
(please do not harass these companies or make it seem like it's their fault, it's not. it's todesktop's fault if anything)
which, if i were to estimate, is probably in the range of hundreds of millions of people in tech environments, other hackers, programmers, executives, etc. making this exploit deadly if used.
the fix
i immediately used my contacts to get in reach with the owner of todesktop, we were chatting via signal and the fix came almost immediately. they were nice enough to compensate me for my efforts and were very nice in general.
the build container now has a privileged sidecar that does all of the signing, uploading and everything else instead of the main container with user code having that logic.
security incidents happen all the time, its natural. what matters is the company's response, and todesktop's response has been awesome, they were very nice to work with.
check out todesktop's incident report here
for those wondering, in total i got 5k for this vuln, which i dont blame todesktop for because theyre a really small company
update: cursor (one of the affected customers) is giving me 50k USD for my efforts.